Google Workspace, Cloud Platform Services
How migrating to the cloud can solve your problem with shadow IT
Many organizations struggle with the widespread use of unauthorized tools, known as shadow IT. While these tools seem like convenient shortcuts, they create a blind spot for data security and can lead to compliance issues. Thankfully, the cloud offers a simple, secure, and cost-effective solution.
Let’s look at the risks and solutions to using unapproved tools for your business.
What is shadow IT?
Shadow IT is the applications or programs employees use for work that the IT department isn’t aware of. This can include file sharing on personal clouds or free video chat apps instead of the company’s approved ones. While handy at times, it can quickly become messy and cause serious security and compliance issues.
Why do employees use shadow IT?
Employees turn to shadow IT for a few reasons, including convenience and familiarity. The company-approved tools may be clunky or lack the features they need to do the job quickly.
Or, perhaps employees are already comfortable using certain free apps in their personal lives and want to avoid the hassle of learning a new system. Sometimes, IT is also slow to approve new tools, which makes employees take matters into their own hands.
Why is shadow IT so risky?
While these tools might seem like quick fixes for employees, they pose several risks:
- Security vulnerabilities: Unauthorized apps often lack the robust security features of IT-approved solutions. This can expose your company’s data to breaches and malware.
- Compliance issues: Shadow IT can make it difficult to comply with industry data storage and access regulations.
- Integration headaches: A patchwork of unapproved apps creates integration nightmares, hindering collaboration and workflow efficiency.
- Lack of IT oversight: IT loses control over data backups, disaster recovery, and user access management.
How can businesses address the shadow IT problem?
There are a number of steps that businesses can take to address the shadow IT problem, including:
- Educating employees about the risks of shadow IT
- Implementing policies and procedures for the use of IT resources (define what types of
- IT resources are allowed, how they can be used, and who is responsible for managing them)
- Providing employees with access to approved IT resources
- Monitoring IT usage to identify and address shadow IT risks
Discover how Kytary.cz eliminated shadow IT by implementing Google Workspace. Read our customer success story now!
How can migrating to the cloud help with shadow IT?
A well-planned cloud migration strategy can be your key to eliminating shadow IT in your organization.
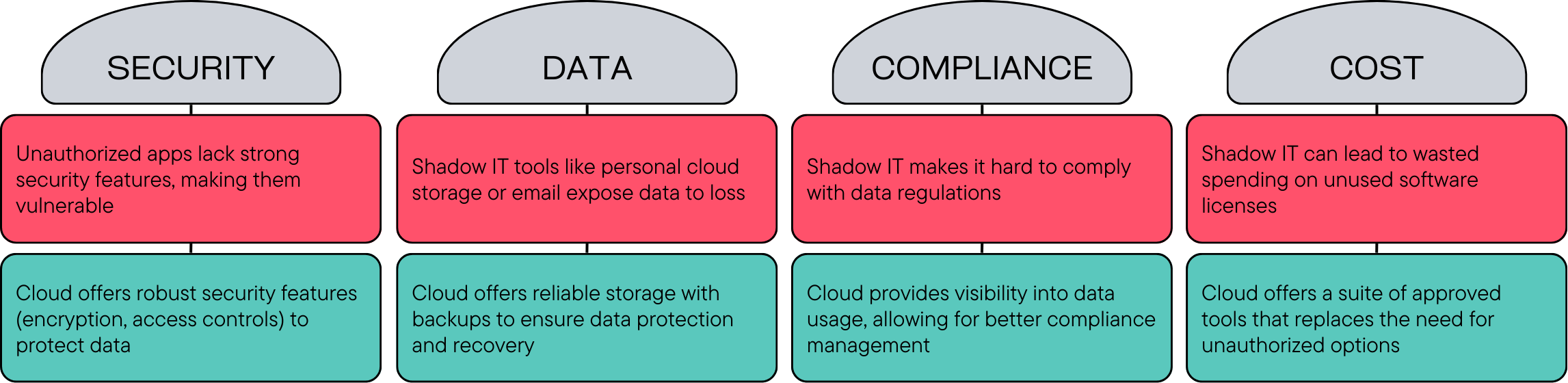
- Security first: Cloud providers offer robust security features like encryption, access controls, and intrusion detection. This minimizes the risk of data breaches and malware infections compared to unsecured solutions like USB drives or personal email accounts.
- Visibility and governance: Cloud platforms offer a centralized view of all applications and data used within your organization. This visibility allows IT to establish clear data storage and access governance policies, ensuring compliance with industry regulations. On the other hand, shadow IT creates a blind spot for IT, making it difficult to enforce these regulations.
- Sanctioned alternatives: Cloud platforms offer a comprehensive suite of IT services, from secure file-sharing and collaboration tools to communication platforms, all within a centrally managed environment.
- Reduced data loss risk: Traditional shadow IT methods like USB drives and personal email are vulnerable to physical loss and data breaches. Cloud storage offers a much safer alternative.
- Better user experience: Modern cloud-based applications are often user-friendly and offer features that may be lacking in traditional IT-approved tools. By migrating to a user-friendly cloud environment with robust capabilities, you can improve employee satisfaction and productivity.
While shadow IT can be an effective short-term solution for your business, it might actually harm you in the long run. Consider moving to the cloud and a centralized approach to keep your data in check. Contact us for a free consultation to discuss the best option for your business.
We partner with JumpCloud, the industry’s leading platform for unified identity and device management for Google Workspace customers, and help you secure your cloud environment. Find out more about our collaboration with JumpCloud here.